Execution Phase
Great! Now that you have installed all the prerequisites, let's get started!
Step 0:
Navigate to Applications -> GPIO -> [ESP32] Wifi Marauder
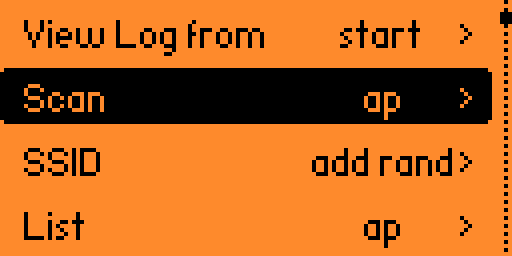
Step 1:
Scan your AP
Step 2:
Select the AP you want to Deauth and Sniff
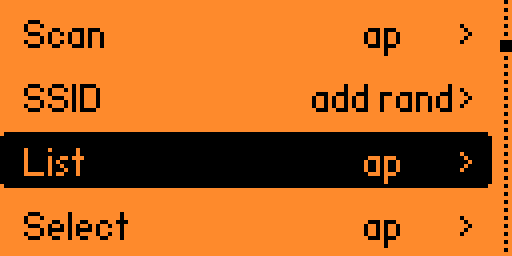
Step 3:
Find your SSID and remember the number beside it.
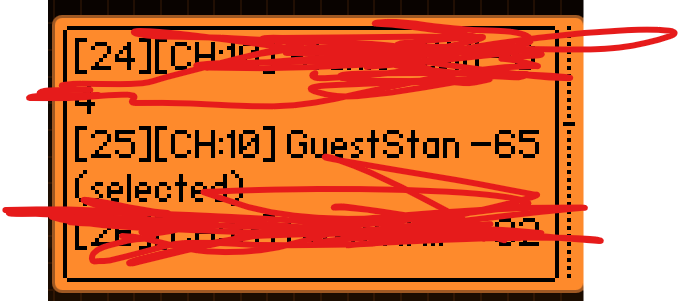
Step 4:
Press on Select and Key in the number beside your SSID. Example: 1
Step 5:
Before you press on the Deauth button, change your Sniff to raw to make sure that you can sniff the handshake.
Step 6:
Get your pcap file from the Flipper Zero and open it with Wireshark.
SD Card -> app_data -> marauder -> pcap -> Sniffraw_1.pcap
Step 7:
Go click on the .pcap file and it will open up Wireshark.
Type on the filter bar: eapol
You should have something like this:
key(Message 1 of 4), key(Message 2 of 4), key(Message 3 of 4) and key(Message 4 of 4)
Step 8:
Go to this website and upload your .pcap file
And download the .hc22000 file.
Step 9:
Drag the .hc22000 file into the hashcat folder.
AND also the cracked.txt.gz file into the hashcat folder (depends on what you want to crack).
Make sure both files are in the same folder.
Open up CMD and CD to the hashcat folder.
Afterward, run this command:
hashcat -m 22000 (your .hc22000 file) (your cracked.txt.gz file)
Your password will be cracked in a few seconds or minutes depending on your computer and the password.
```